CIO, CTO, CSO, IT Service Management, IT Job Description, Sarbanes Oxley, and IT Salary News
CIO - CTO - CSO News
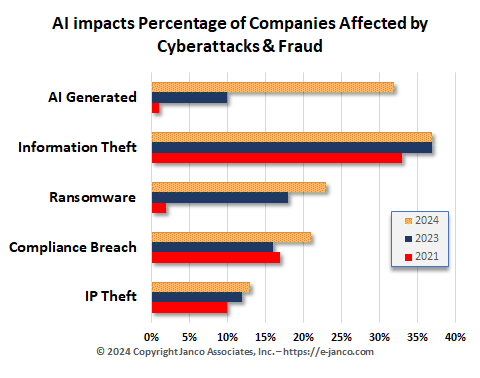
Cyberattackers use AI to increase attacks
More companies have faced ransomware attacks as cyberattacks are AI generated
There has been an increase in AI-generated phishing attempts and other cyberattacks. To get the base of knowledge, attackers may have electronically read scores of press releases, company correspondence to customers, and other CSR data from companies to get the right mix for their attacks. That has significantly improved the generative AI used to base their attacks.
A human-crafted phishing email takes an average of 16 hours to create. By comparison, AI can generate deceptive high-quality phish in a few minutes.
This is increasing the number of ransomware attacks. Attacks hit record highs in 2023 despite falling payment rates, as attackers scaled up the number of attacks and new AI weapons were brought to bear on both sides of the war, promising to make an even bigger impact this year.
Ransomware payments were over $1.1 billion in 2023 or twice what they were in 2022. The frequency, scope, and volume of attacks were all up in 2023. Also, the number of independent groups conducting the attacks increased dramatically, according to one research firm.
The size of each payment is up, with more than 70% of all payments totaling $1 million or more. However, more companies are refusing to pay ransoms and restore from backups. It is estimated that just under 30% of victims paid up in the fourth quarter of 2023, down from 85% in 2019. This data comes from the insurance industry.
Read on Order Security Manual Template
- more info
Cyber Attacks on the rise
Cyber Attacks increased in 2023 and trend continues in 2024
Data breaches, malware attacks, and mandated requirements are an everyday issue for organizations as the move towards e-commerce and Blockchain architecture. With all of the additional demands this places on the technology processing functions, C-level executives are demanding that the CIO, CISO, and CTO have in place tools to address these compliance and security issues.
Cyber attacks rose by over 30% in 2023. Global Threat report by Crowdstrike reported the types of attacks were
- Cloud-conscious attacks up by 110%
- Cloud environment inclusions up by 75%
- Number of victims named on eCrime leak /sites 76% on year-to-year analysis
- The number of attacks that had ransomware focus up by 84%
They also reported that the problem was not malware rather there was an increase in the number of attackers. Some were state-sponsored and others originated in countries that were not averse to providing cover for the attackers as 61% of attackers were against the US and 11% to Europe.
Countries that were sources of those attacks were Russia, China, North Korea, Syria, Iran, Pakistan, Georgia, Columbia, and Turkey.
Jancos Security Manual template and Compliance Management Tool Kit provide solutions and methods of protection.
Order Cyber Attack Protection Download Selected Pages
- more info
AI Managers and technoligists are in Demand
KPI Metrics Key for Artificial Intelligence Managers
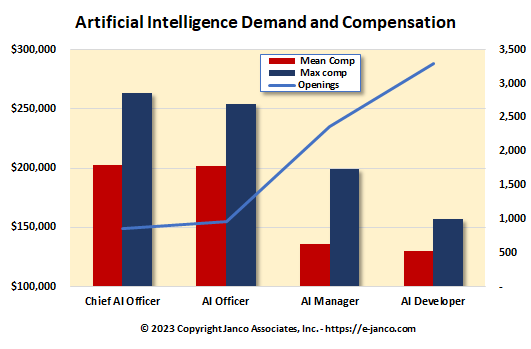
IT decision-makers are optimistic about the potential benefits of infusing enterprise applications with generative AI. This is driing the demand for executives and managers who have direct AI experience.
Almost 90% of all CIOs and CTOs have either implemented AI and generative AI technologies in their organizations, have plans to, or are actively researching them. Enterprises are looking to AI to boost productivity and innovation, and one-third of organizations with an interest in the technology have hired or are looking for a chief AI officer.
Over 3/4 of all CIOs are preparing for the arrival of generative AI in a number of ways, with 57% identifying use cases, 45% starting pilot programs, 41% training or upskilling employees on it, 40% establishing policies and guidelines.
One third of CIO's interviewed by Janco already have generative AI tools in users' hands, and may others say they are testing apps from vendor partners.
Read On AI Manager Order Manager AI Job Description
- more info
Artificial Intelligence IT Pros Salaries over $100K
Managers with AI Expertise command six figure salaries
Experienced Artificial Intelligence and Machine Learning IT Professionals are in high demand. Salaries for those professionals are well into the low six figures. Salaries for management positions with AI skills are in the $150K to $250K range. Experienced managers and developers are getting offers in the $125K to $165K range.
Order Salary Survey Download Sample
- more info
Best Practices New Technology Implementation and Deployment
New technologies like AI implementation and deployment have unique risk profiles
When new technologies appear they are often misunderstood. Early innovators face a new issues and often are costly to be first on the block. However, if developed and deployed in a timely manner they can be a competitive advantage and a way to identify the enterprise as an industry leader.
Top 10 Best Practices for new technologies
- Tie technology to the business's operational objectives
- Align the new technology with the business's strategic plan
- Have a big picture of the future
- Build the infrastructure, governance, and culture to support the new technology
- Have an organization that is used to success
- Have the right skills in place
- Implement incrementally to prove concepts have value and work
- Understand the risk profile of the new technology
- Kill new technology efforts when they flounder
- Question status quo
Read On Order IT Governance Infrastructure
- more info
C-Level executives targeted by EvilProxy
EvilProxy - phishing as a service attacks target c-Level executives
The EvilProxy phishing page, masquerades as a Microsoft 365 login page. EvilProxy functions as a reverse proxy, where the service is positioned between the user and the real login page, relaying requests and responses back and forth between them. From the victims perspective, it's like they're interacting with the real website, but the attacker gets to see everything that gets transmitted between the two parties, including the login credentials and MFA codes. EvilProxy claims to be able to bypass MFA on Apple, Gmail, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and other popular websites.
Of the accounts that were accessed by attackers, 39% were C-level executives, 17% were chief financial officers, and 9% were presidents and CEOs. When it came to lower-level management and personnel, the attackers focused on users with access to financial assets or sensitive information.
Read on Order Security Manual Sample
- more info
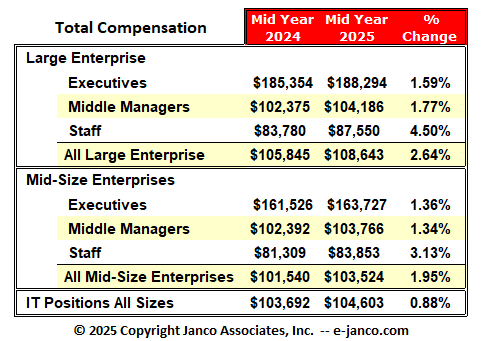
IT Salaries expected to rise in 2023-2024
Number of IT Pros who are unemployed in the US is low
We have found, as the talent shortage grows and inflation continues, salaries for highly skilled tech workers will continue to rise. In fact, compensation could increase by 8% for some roles in 2023-2024, according to our recent salary survey.
Read on Salary Survey Order Salary Survey Download Summary
- more info
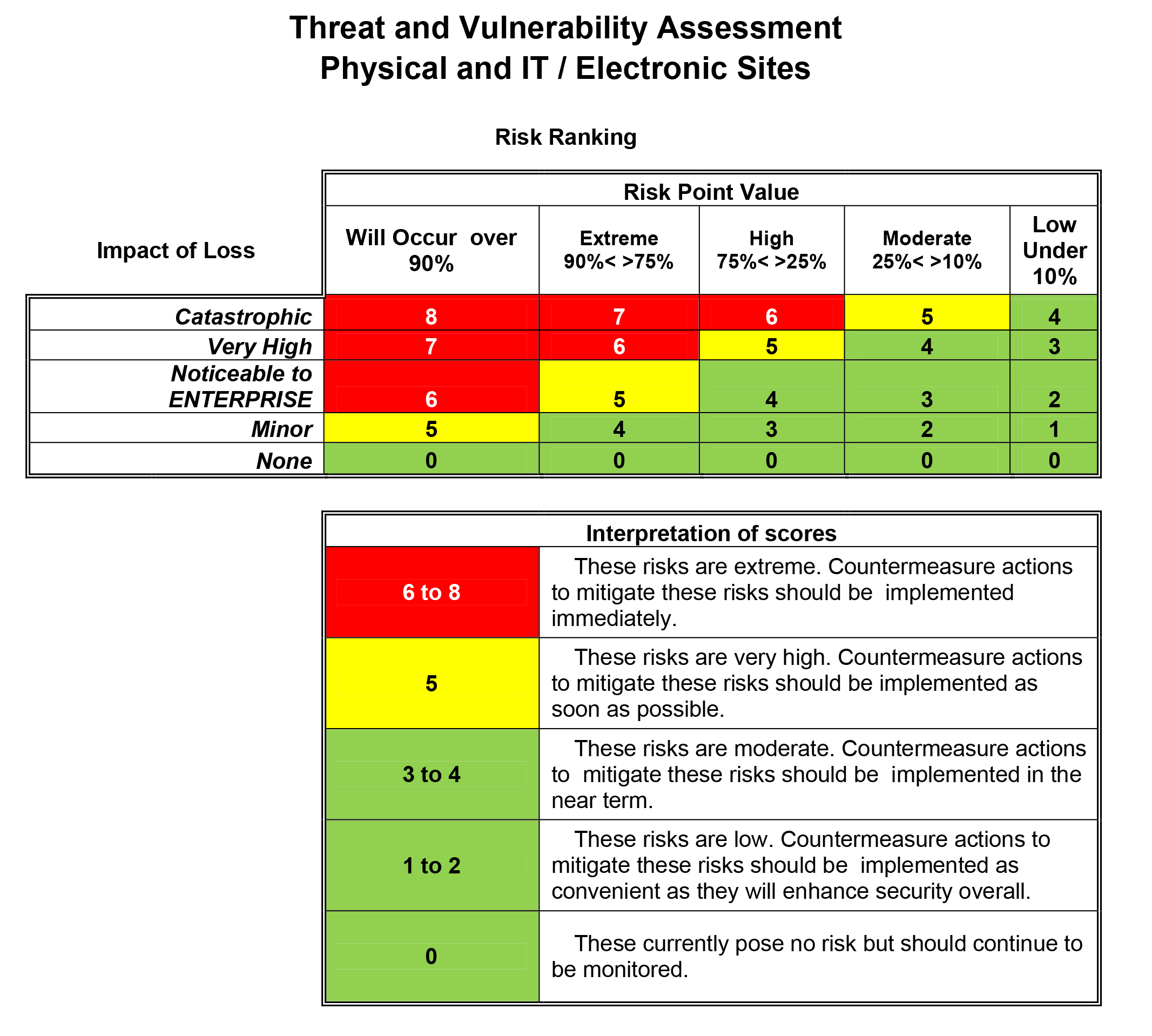
C-Level executives hold CIOs accountable for security breaches
Tools for the CIO and IT Managers to better manage security exposure
Recent hacks have place a new emphsis on security risk factors. C-Level executives want to know what risks they face. Many are asking for Risk Scores. The issue is that existing KPI metrics do not help to address security risk in a way that is meaningful.
The constant stream of high profile breaches and the resulting class action lawsuits, negative PR, loss in share price, cybersecurity insurance pay-out refusals, and even termination of liable executives has made this an urgent priority.
Order Threat Vulnerability Tool Download Selected Pages
- more info